My first post detailed the foundation of this blog, but today we're diving deep into WordPress security hardening. A secure connection is just the beginning. The real challenge lies in building a multi-layered defense system that protects the server, the network, and the application itself.
However, a secure connection is just the beginning. The real challenge lies in building a multi-layered defense system that protects the server, the network, and the application itself. This post is a deep dive into the specific steps I took to harden this WordPress installation—the “how-to” behind the security architecture.
It's also a story of trade-offs. While my security scores are excellent, my initial performance scores on GTmetrix are... a work in progress.
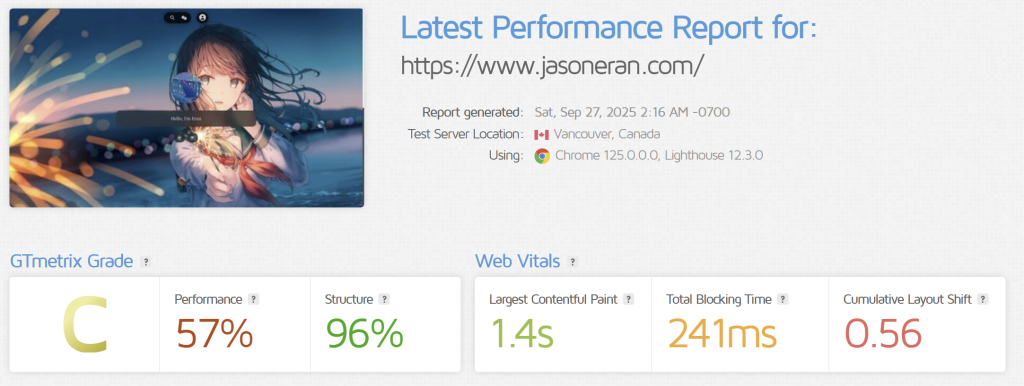
The report pinpointed the main culprit: the beautiful, dynamic hero image at the top of my site. It's a core feature of the Sakurairo theme, but its random nature intentionally breaks caching, which significantly impacts performance metrics like Cumulative Layout Shift (CLS). For now, I've decided to keep this aesthetic feature, and I'll tackle the challenge of optimizing it in a future post. It's a perfect example of the classic developer dilemma: features vs. performance.
Today, let's focus on what is working perfectly: the security.
Layer 1: The Fortress - Origin Server Hardening
I believe a server should be secure even if it's sitting naked on the internet. My first steps were to lock down the Linux environment itself.
- SSH Hardening: I disabled direct root login and password authentication entirely, switching to key-based authentication only. This eliminates the risk of brute-force password attacks on the most privileged account.
- Automated Defense: I installed
fail2ban. This utility constantly monitors system logs and automatically bans any IP address that shows malicious signs, like repeated failed login attempts. - Firewall & Origin Shield: This was the most critical step. The server's firewall (Alibaba Cloud's Security Group) is configured to only accept web traffic (ports 80 and 443) from the official IP ranges of the ESA/CDN network. All other traffic is dropped. This hides the server's true IP and ensures all traffic is filtered by the WAF first.
Layer 2: The Elite Guards - ESA Pro WAF Configuration
The Edge Security Acceleration (ESA) platform acts as my primary line of defense. I went beyond the defaults and configured a set of custom WAF rules for active threat prevention.
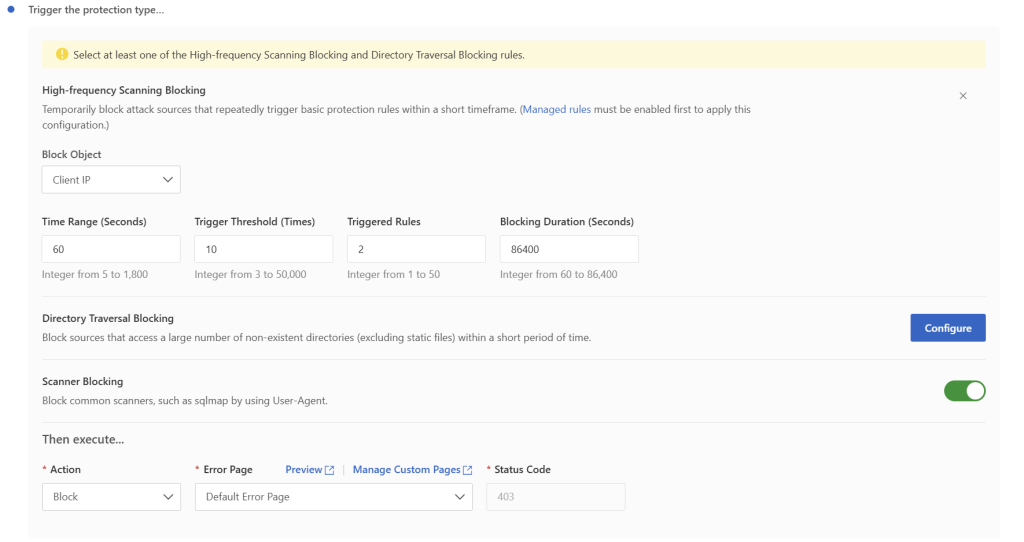
Anti-Brute Force: I created a rate-limiting rule specifically for wp-login.php. Any IP attempting to log in more than 10 times within a minute is automatically blocked for an hour.
Anti-Scanning: I enabled modules that detect and block common scanner tools (like sqlmap), directory traversal attempts (searching for non-existent sensitive files), and other automated probing behaviors.
Intelligent Rate Limiting: I activated the "Smart Rate Limiting" feature. It uses machine learning to establish a baseline of normal traffic for my site and then uses a JS Challenge to gracefully filter out bots and abnormal traffic spikes without blocking real users.
Layer 3: The Inner Sanctum - WordPress Application Security
Finally, I hardened WordPress itself.
- Wordfence Security: I installed this excellent plugin as a final application-level firewall and malware scanner. The key configuration here was teaching Wordfence to correctly identify the real visitor IP from the
X-Forwarded-Forheader sent by ESA, so its blocking logic would be accurate. - Nginx Configuration: I added a specific rule to my Nginx site configuration to deny all access to hidden files (those starting with a dot), preventing exposure of sensitive files like
.user.ini.
# Deny access to all hidden files
location ~ /\. {
deny all;
}
What’s Next?
My security journey isn't over. The next logical step, as pointed out by the Mozilla Observatory report, is to implement a robust Content Security Policy (CSP). This will be a complex but rewarding challenge, and I look forward to sharing my findings in a future article. And of course, I have that fascinating performance puzzle to solve!
Putting It All Together: My WordPress Security Hardening Philosophy
Ultimately, a complete WordPress security hardening strategy is about more than just installing a plugin; it's a holistic approach that involves every layer of the architecture. From using a cloud WAF at the edge to locking down the origin server, every step contributes to the final result. This comprehensive process is the foundation of modern WordPress security hardening.
Final Thoughts
Building a secure website is a continuous process of layering defenses. No single tool is a silver bullet. It's the combination of a hardened server, an intelligent cloud WAF, and a secured application that creates a truly resilient platform.
This setup gives me peace of mind and a solid foundation to build upon. I hope sharing these details is helpful. What are your go-to security measures when setting up a new website? I’d love to read your thoughts in the comments.
— Jason Eran



Comments NOTHING