Hello, world! This post documents my journey in creating a truly secure WordPress setup from the ground up. I wanted to build a platform that was not only fast, but also architecturally sound, and this is the story of how I did it, achieving an A+ on the industry-standard SSL Labs test.
When I decided to launch this blog, I set a personal challenge: don't just build a website, build a professional-grade, modern web application. I wanted to go beyond a simple "one-click install" and create a platform that was not only fast and secure but also architecturally sound.
This post is the story of that journey. It's a look under the hood at the technology and the "why" behind the choices I made to get jasoneran.com up and running, achieving an A+ on the industry-standard SSL Labs test and uncovering the next steps in application security.
The Blueprint: My Choices for a Secure WordPress Setup
After some research, I settled on a decoupled, cloud-native architecture. My goal was to combine the power of a dedicated server with the resilience and performance of a global edge network.
Here’s the stack I chose secure WordPress setup:
- Cloud Provider: Alibaba Cloud. I opted for their Lightweight Application Server as a starting point—a simple but powerful VPS.
- CDN & WAF: Alibaba Cloud's Edge Security Acceleration (ESA) Pro. I wanted to explore an integrated solution that combined a global CDN, a robust Web Application Firewall (WAF), and Dynamic Content Delivery (DCDN) capabilities.
- CMS: WordPress. It’s the undisputed king for a reason. Its vast ecosystem and flexibility make it a great foundation.
- The Stack (LNMP):
- OS: Alibaba Cloud Linux (a CentOS derivative).
- Web Server: Nginx.
- Database: I upgraded from the EOL MySQL 5.7 to MySQL 8.0.
- Runtime: I upgraded from the default to PHP 8.2.
The Build: Key Milestones and Learnings
Building the platform was a multi-layered process, focusing primarily on two areas: relentless security hardening and obsessive performance optimization.
Part 1: A Defense-in-Depth Approach to Security
My goal was to create a fortress, but one with many layers of security, not just a single high wall.
- At the Edge (ESA WAF): The first line of defense is the cloud WAF. I configured a suite of proactive rules, including anti-brute force protection for
/wp-login.php, anti-scanning modules, and intelligent rate-limiting. - At the Origin (Server Hardening): I believe the origin server should be able to defend itself. I hardened SSH by disabling root login, set up
fail2banto block malicious IPs, and configured the server’s firewall to only accept web traffic from ESA’s official IP ranges, effectively creating an “origin shield.”
# Deny access to all hidden files
location ~ /\. {
deny all;
}
- At the Application (WordPress): I installed Wordfence as a second layer of defense. The biggest challenge here was configuring it to correctly identify the real visitor IP passed through ESA's
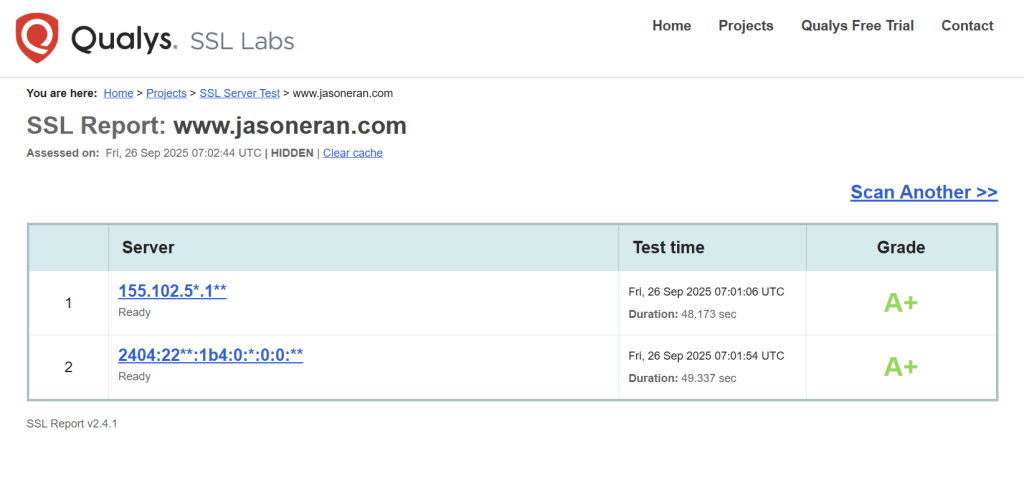
X-Forwarded-Forheader, ensuring its blocking mechanism works accurately. - The Encryption & Security Headers: A major milestone was achieving an A+ score on the Qualys SSL Labs test. This confirms the core transport-layer security is world-class, thanks to a modern TLS v1.2+ policy and the implementation of HSTS.However, securing the connection is only half the battle. The next level is application security, which is where tools like the Mozilla Observatory come in. My initial scan revealed that while many headers like
X-Frame-OptionsandReferrer-Policywere correctly implemented by ESA's managed rules, there were still areas for improvement—most notably, the implementation of a Content Security Policy (CSP). This was a fantastic learning moment, showing that even with a secure connection, there are deeper layers to protect against attacks like Cross-Site Scripting (XSS).
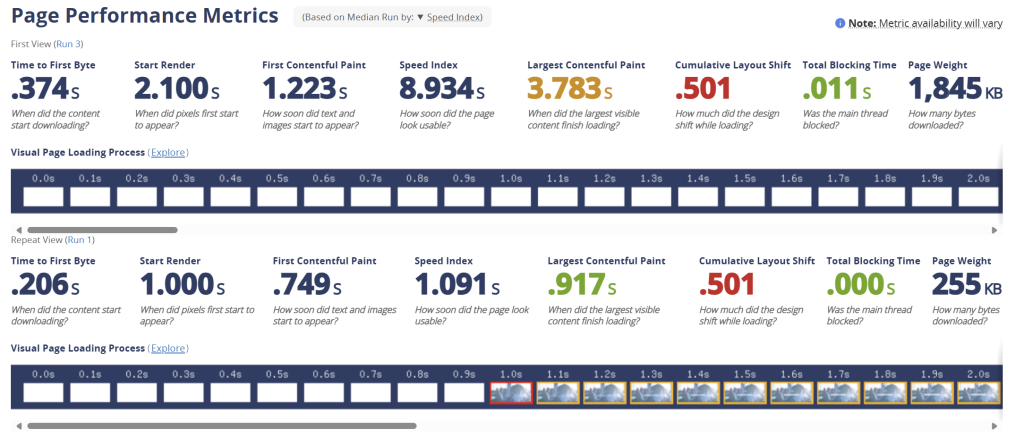
Part 2: The Quest for Global, Millisecond Speed
I'll cover my performance optimizations and the excellent WebPageTest results in a separate, upcoming post, as there's too much to share here!
Challenges & "Aha!" Moments
The journey wasn't always smooth. I wrestled with stubborn 502, 521, and ERR_TOO_MANY_REDIRECTS errors. Troubleshooting these taught me more about how cloud firewalls, reverse proxies, and server configurations interact than any textbook could. The "aha!" moment in my secure WordPress setup was realizing a persistent 521 error was caused by the server's firewall blocking the CDN's own IP addresses—a classic mistake when setting up an origin shield.
Troubleshooting these errors was a deep dive, and I plan to write a detailed guide on that process.
What's Next?
My immediate next step is to tackle the Content Security Policy. A CSP is a powerful but complex feature that requires carefully defining all the legitimate sources for scripts, styles, and images. My goal is to implement a strict policy without breaking the site's functionality, and I'll be sharing my process in a future post.
Beyond that, I plan to venture into the AI playground by integrating Alibaba Cloud's Bailian LLM to create a custom AI assistant for the blog.
Final Thoughts
Building this blog has been an incredible learning experience, and I'm happy to share the results of my complete secure WordPress setup. It solidified my belief that creating a website today is less about installation and more about architecture. Every component, from DNS and TLS to caching and application-level security, is a piece of a larger puzzle.
This is just the beginning of my journey, and I'm excited to share more of what I learn here. I'd love to hear about your own experiences in building web projects. What tools do you love? What challenges have you faced? Please feel free to leave a comment below.
Thank you for reading!
— Jason Eran


